In a recent alert, the Authority of Information Security (Ministry of Information and Communications) has urged agencies, organizations, and enterprises in Vietnam to review and identify systems impacted by nine new security vulnerabilities found in Microsoft products.
The National Cybersecurity Monitoring Center (NCSC) under the Authority of Information Security periodically conducts analysis, evaluation, and issues alerts regarding security vulnerabilities in Microsoft products, particularly those with high and critical impacts, following Microsoft’s regular release of security patches.
Microsoft released its October patch update on October 8, disclosing a total of 121 new security vulnerabilities, including 117 in its products and four in third-party products that affect Microsoft systems.
The NCSC’s assessment highlighted nine security vulnerabilities requiring special attention due to their high and critical impact levels. Out of these, seven vulnerabilities could enable remote code execution (RCE). These include:
- CVE-2024-43468 in ‘Microsoft Configuration Manager’
- CVE-2024-43582 in ‘Remote Desktop Protocol Server’
- CVE-2024-43572 in ‘Microsoft Management Console’
- CVE-2024-43504 in ‘Microsoft Excel’
- CVE-2024-43576 and CVE-2024-43616 in ‘Microsoft Office’
- CVE-2024-43505 in ‘Microsoft Office Visio’
Additionally, CVE-2024-43583 in ‘Microsoft Winlogon’ allows attackers to escalate privileges, and CVE-2024-43573 in the ‘Windows MSHTML Platform’ facilitates spoofing attacks.
Notably, detailed information on CVE-2024-43583 has been made public, and CVE-2024-43572 and CVE-2024-43573 are actively being exploited.
The Authority of Information Security has stated that these high and critical vulnerabilities could be exploited to conduct unauthorized actions, posing risks to the security of information systems within agencies, organizations, and enterprises.
The recommendation for Vietnamese entities is to inspect and review computers running Windows OS to identify any potential vulnerabilities. If impacted, the best mitigation is to apply the latest patches as directed by Microsoft.
The agency also advised organizations to bolster their monitoring capabilities and be ready to respond promptly to any signs of exploitation or cyber-attacks. Additionally, maintaining vigilance by regularly following alerts from relevant authorities and major cybersecurity organizations is essential for timely identification of threats.
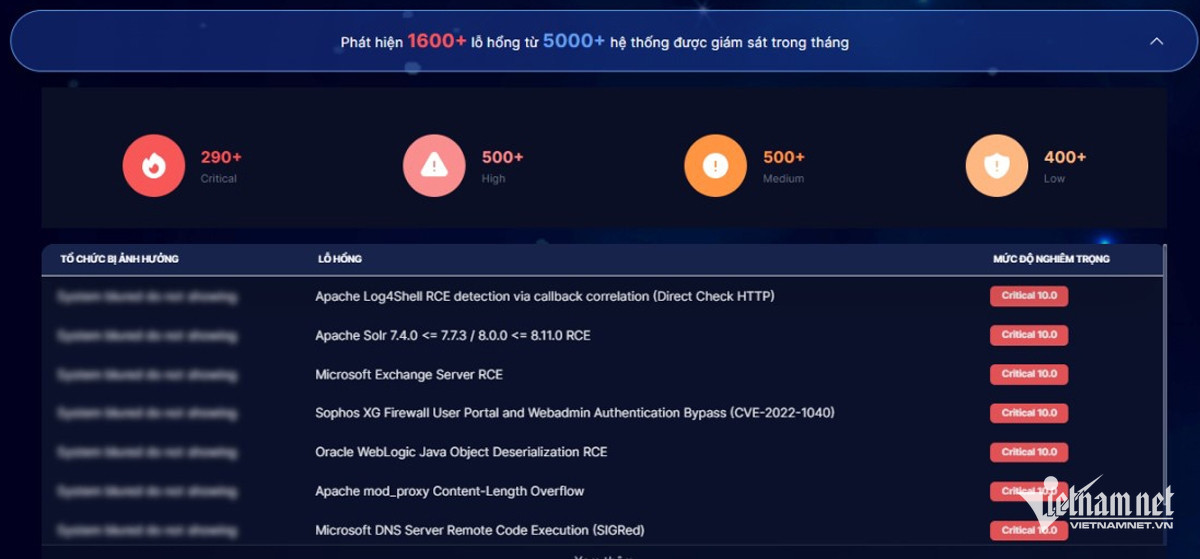
According to a recent cybersecurity status report from the Authority of Information Security published on the National Cyber Space Portal on October 14, the NCSC’s remote monitoring system identified over 1,600 vulnerabilities across 5,000 publicly exposed systems in September 2024.
In September alone, the NCSC recorded 12 newly disclosed security vulnerabilities with significant and high impact levels, which could be exploited by malicious actors to target systems within local agencies and organizations.
The agency emphasized that these vulnerabilities exist in commonly used products across various agencies, organizations, and enterprises.
“We urge all units to conduct thorough system checks and assessments to determine if their systems use affected products and promptly implement remediation measures to safeguard information security. Continuous updates on new vulnerabilities and cyber-attack trends are also crucial,” recommended the Authority of Information Security.
Van Anh